Key card systems incorporate various technologies to provide a more secure form of access control to both the hospitality and business sectors. The card’s digital authentication provides extra security and ease of use. A card will not just replace locks, but improve a location’s security and privacy.
In this article, you’ll discover how to best leverage key cards, strategic optimization to get the most out of them, and how to benefit from their security features.
Table of Contents:
- Understanding Modern Key Card Technology
- The Strategic Importance of Key Card Systems
- Different Types of Key Card Technologies
- Key Benefits of Implementing Key Card Access Systems
- Innovative Applications of Key Card Technology
- Essential Security Features of Key Card Systems
- Implementation Best Practices for Key Card Systems
- Hotel Door Locks: Complete Overview of Modern Security Systems
- Hotel Door Stoppers: Essential Guide to Room Security
Understanding Modern Key Card Technology
Key card implementations come in a variety of different forms. From a standard access card to a tightly integrated hotel door lock system. However, encoded credentials are the basic element found in all key cards. All of the technologies that use the cards provide a method of reading and acting on data stored within them.
This can range from simply unlocking a lock to opening up a variety of methods for real-time monitoring and modification of access permissions. Likewise, the cards allow for real-time monitoring and logging of access to any given area.
The Strategic Importance of Key Card Systems
Key card systems provide significant monetary, efficiency, and informational advantages. The most obvious benefit of an electronic key is its security elements. Electronic access systems are inherently superior to traditional analog locks. You have options to instantly change access rules, obtain logs of who’s entered a room, and revoke access.
However, the systems are also more secure. Analog keys come with a number of issues, from duplication to loss. Meanwhile, an electronic system reduces fees associated with physical keys while providing higher levels of security – likewise the digital access ties into management systems.
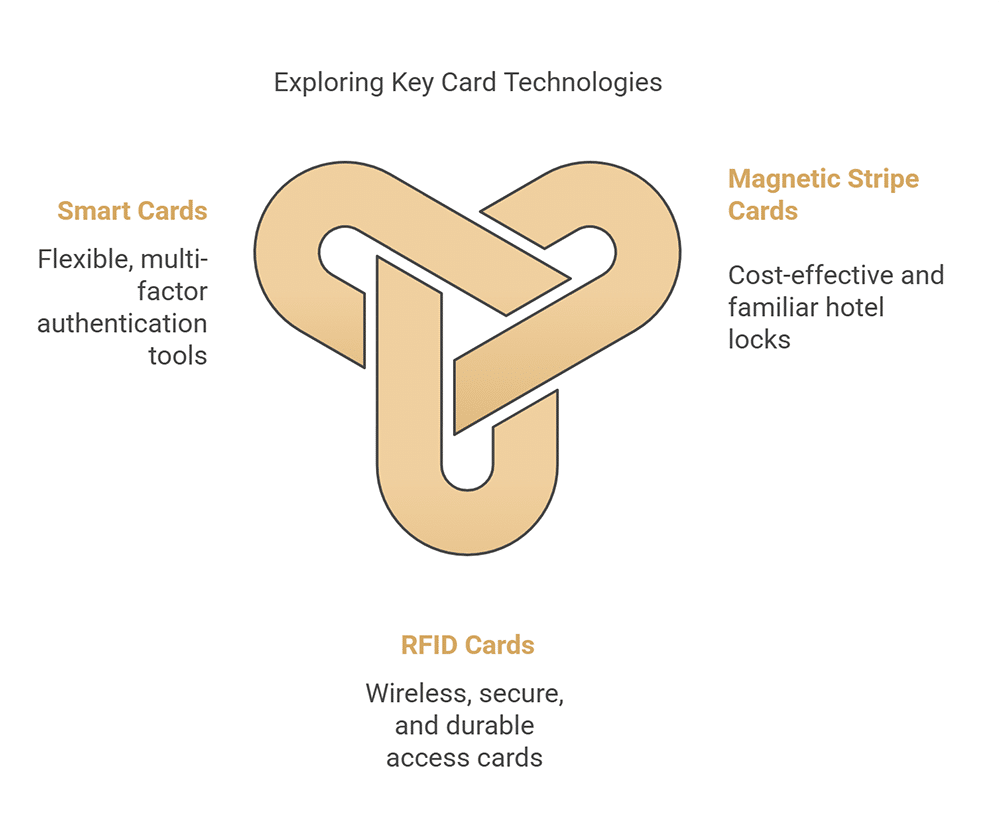
Different Types of Key Card Technologies
You’ve seen some of the foundational elements that make key card systems so important. However, there are a lot of additional benefits to be found in the following types.
Video: What is a Key Card System?
Magnetic Stripe Cards
A magnetic stripe key card keeps its data within a small magnetic band. This technique is similar to what you see on the back of a standard credit card. Using the key is as simple as swiping it through a card reader. It’s a cost-effective, reliable, and easily understood technology. They’re often used for a hotel lock system since guests will already be familiar with how to swipe the cards. Likewise, the system’s simplicity makes it easy to repair the readers. However, over time the card’s magnetic stripe will wear out and require a replacement.
RFID Cards
RFID cards are a wireless take on the concept of a key card. An RFID card can transmit information to a reader through encrypted radio frequencies. This technology brings with it a number of advantages. The wireless nature of RFID means that the cards aren’t subject to the same wear and tear as magnetic stripe cards and will, therefore, last longer. On top of that, the card’s use of encryption makes it especially secure and resistant to duplication. The cards are also easy to use as they don’t require specific points of contact with a reader.
Smart Cards
Smart cards are the cutting-edge of key card technology. These cards work through tiny embedded microprocessors. The fact that this form of digital key can actually process information means that it comes with unprecedented flexibility. The cards can store far more information in a wider variety of formats. They can offer more powerful data security and seamlessly integrate with a variety of management systems. A smart card can even support multiple authentication factors at the same time. A smart card is arguably both the most flexible and the most secure at the same time.
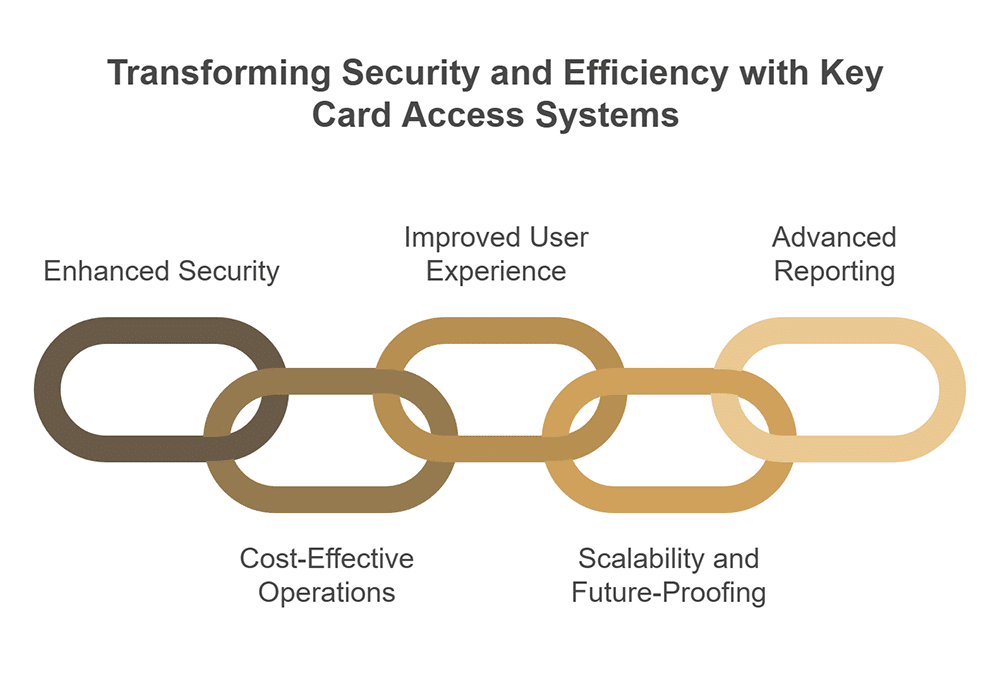
Key Benefits of Implementing Key Card Access Systems
There’s a variety of different types of key cards and methods to integrate them within a property. Choosing between them means understanding the following benefits.
Enhanced Security Control
Key card implementations give you real-time control and monitoring along with secured digital authentication methods. The combination of these elements means that the system will help prevent problems while also informing you when they occur so that you can instantly take control. You’re automating the security while also ensuring that the human element is still in the picture. And security can be taken even further by linking the card system to video surveillance, alarms, and more. Combined with logging functionality this will ensure that you have a solid network of monitoring and security protecting everything.
Cost-Effective Operations
The fact that key card systems are digital provides a number of financial benefits. The most obvious advantage is the lack of required maintenance for physical keys and locks. The cost of key cutting and lock replacement can be cut by implementing digital systems. The extent of these savings scales to the size of the property. Additionally, hotels will find that digital systems provide lower maintenance costs and administrative overhead. The fact that digital systems can also integrate into the larger hotel management system also increases operational efficiency, which translates into direct savings for the property.
Improved User Experience
Modern key card implementations make things easier for management, employees, and guests. Key cards are user-friendly and simplify procedures for staff. An employee can carry a single card to use on every door, with the system tracking where they’re allowed to go. Likewise, guests are able to use a key card in almost no time at all. The user-friendly nature of the card system means that guests and staff will have a more enjoyable experience. Likewise, security concerns are streamlined by the addition of digital authentication. They’re equally easy to integrate into management systems.
Scalability and Future-Proofing
Growth is one of the most significant benefits of digital systems. As the size and scope of a property grows, so does its need for security. Key card systems can easily scale to match the growth of a business. In addition to its nature as a digital resource, key cards are also able to scale due to their modular qualities. The systems can be easily integrated with various technologies and software systems. As new technologies come into play, it’s simply a matter of plugging them into the existing key card implementation to leverage their benefits.
Advanced Reporting and Analytics
A key card implementation can log its interactions into a full data set which can be integrated into a variety of different systems. Some of the metrics that are typically logged are usage patterns, security events, and unusual access attempts. The data can be utilized by different systems to provide specially tailored reports to different departments or stakeholders. You can even obtain a real-time view of occupancy levels or move the view into historical data for security audits or managerial planning. Having the data available for analysis also aids in regulatory compliance and strategy.
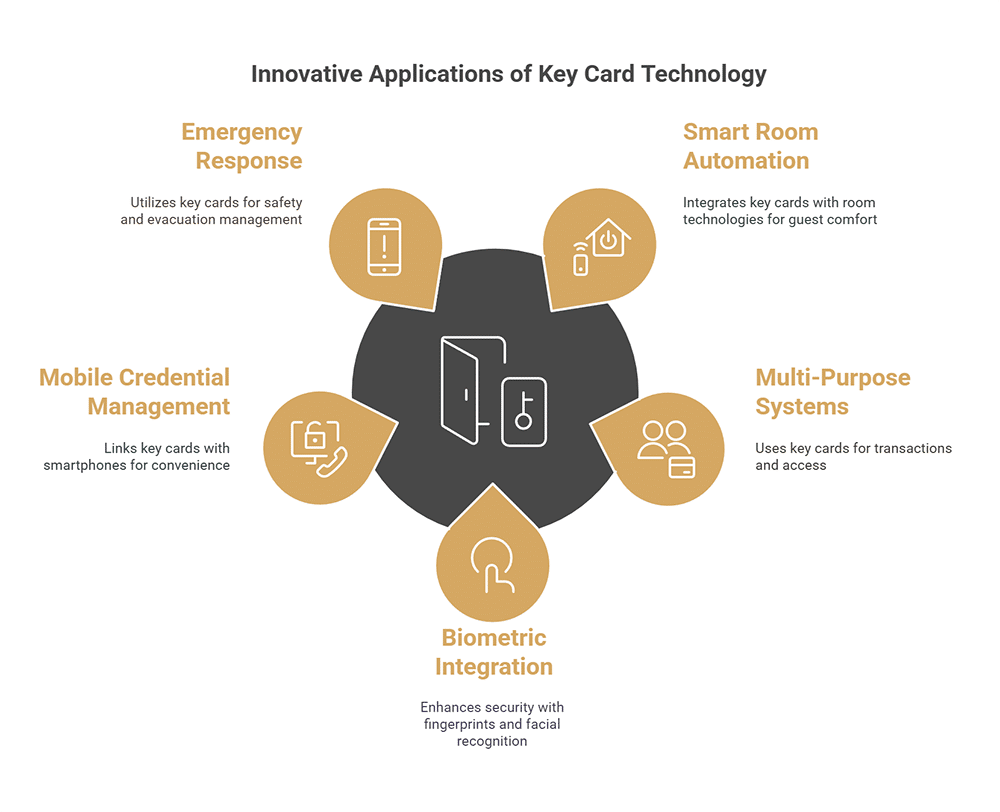
Innovative Applications of Key Card Technology
While key card systems are best known for their role in access control, that’s just the beginning. The following innovations show the system’s impressive flexibility.
Video: NFC vs. RFID: What’s the Difference?
Smart Room Automation Control
Smart rooms consist of interlinked technologies that adjust a room to meet the guest’s needs. Key card systems can act as the central component of these special rooms. The smart room’s various solutions can be activated through use of the key card and perform functions such as climate control, amenity options, and lighting adjustment. Integrating cards with smart room technologies can increase guest satisfaction while also reducing overall operational costs. Rooms that understand a guest’s needs can then automatically adjust themselves without requiring manual instruction. In doing so the rooms reduce excess usage expenses.
Multi-Purpose Transaction Systems
A key card system can also act as an identification and transaction tool. These multi-purpose systems let you use key cards for time tracking, resource usage or management, and payment. It essentially orients vending machines, general facility services, point-of-sale implementations, and more around the key cards while maintaining a high level of security. This type of integration is especially valuable as it reduces complexity and simplifies the management of a facility. At the same time, it streamlines many of the routine tasks people go about during their day through larger-scale integration with all the systems.
Contactless Biometric Integration
Biometrics uses elements of your own body as a method of identification and security. Fingerprints and facial recognition are two of the most commonly used forms of biometric authentication. The more advanced key card implementations can leverage biometrics to add another layer to their security. Combinations of biometrics with key cards are typically leveraged within high-security areas. While this is a more advanced and technically demanding solution, it offers a number of benefits. First and foremost among the benefits is the added security for authentication. However, the contactless nature also makes them considerably more user-friendly.
Mobile Credential Management
Another common integration using key cards can be seen with mobile devices such as smartphones. These integrations typically work through Bluetooth and NFC protocols and can leverage the device’s built-in multi-factor authentication. The biggest advantage of this convergence comes from its overall convenience. People in both managerial and user positions typically find mobile credential management to be extremely user-friendly. The users benefit from being able to use their own, familiar, phones. And the people managing the system benefit from factors like remote credential updates and the ability to remove or grant mobile credentials almost instantly.
Emergency Response Integration
Key card systems can be integrated into emergency response to help manage everyone’s safety. For example, an emergency might necessitate evacuation of the building. Key card authentication can be used to ensure people aren’t moving toward the source of danger instead of away from it. Likewise, this process will generate reports that can be used to inform emergency services as to the number and location of people within danger zones. The real-time nature of card monitoring also makes it an invaluable tool to help educate every party on the ever-changing status within the affected environment.
Essential Security Features of Key Card Systems
Understanding the following foundational elements of security in key card systems will help you get the most out of them:
- The encryption used by key card systems can leverage military-grade algorithms to ensure data isn’t intercepted, stolen, or duplicated.
- Multi-factor authentication can integrate different measures such as PIN, mobile authentication, and biometrics to authenticate users and optimize security.
- Attempts to access a lock can be written in real-time to provide auditable logs or alerts for individuals attempting to break in.
- Centralized remote management gives you the ability to disable potentially compromised cards, change access levels, or alter security measures.
- Anti-tailgating leverages timing and sensors to ensure people can’t bypass security through piggybacking or shared credentials.
- Use precise configuration and controls to customize key cards for time-zone or area-based restrictions.
Implementation of Best Practices for Key Card Systems
Additionally, you should implement the following best practices with your key card systems.
- Perform regular system audits on a quarterly basis to update security measures, judge potential vulnerabilities, and check card reader health.
- Install and maintain redundant power systems to fall back on if the primary power fails.
- Staff training should regularly go over emergency procedures, security rules, and how to handle key cards.
- Create preventative maintenance schedules to test backup systems, readers, and controllers.
- Perform bi-annual audits of access level hierarchy which will check the validity of assigned levels and remove any permissions that have become outdated.
- Create documentation standards for security incidents which will provide instructions to track, investigate, and resolve problems at all levels.
Hotel Door Locks: Complete Overview of Modern Security Systems
Security is a fundamental priority within the hotel industry. As such, it should come as no surprise that security and locks are an important subject among hoteliers. Experts have determined how to implement locks to optimize security and integrate them within a larger property management system. Modern security uses a more holistic approach where the property’s security is all tightly integrated.
You can learn more about how to implement a hotel door lock system in the article “Hotel Door Locks: The Main Lock System Types and Their Benefits”.
Hotel Door Stoppers: Essential Guide to Room Security
Key card systems are only one part of a solid access control policy. The best security implementations also use hotel door stoppers. The devices are mounted on walls, floors, or hinges to control door movement. While traditionally used to protect walls from door handles, they’re also capable of use as an alarm system to augment other security policies like a key card implementation.
You can find out more about how to use hotel door stoppers in the article “Hotel Door Stopper: Definition, Uses, Benefits and the Main Types”.
Did You Like This Article about the Key Card?
You might also be interested in the following articles:
- Ways to Transform a Hotel Room Into a Smart Room
- Types of Hotel Rooms: The Different Hotel Accommodation Types
- Hotel Room Category: Learn About Categorizing Hotel Rooms
- Hotel Room Types & Room Pricing Tips for Hoteliers
- Types of Rooms in a 5-Star Hotel: Exploring the Most Common Options
Key card systems are powerful, but they also require some planning to get the most out of them. Take some time to consider what you’ve learned and how to best implement it.
More Tips to Grow Your Business
Revfine.com is the leading knowledge platform for the hospitality and travel industry. Professionals use our insights, strategies, and actionable tips to get inspired, optimize revenue, innovate processes, and improve customer experience.Explore expert advice on management, marketing, revenue management, operations, software, and technology in our dedicated Hotel, Hospitality, and Travel & Tourism categories.








Leave A Comment